Steve is a CTO and Chief Architect who has spent the last 12 years working for HMG within UK National Security. Currently at Sopra Steria as the CTO on a large defence programme, Steve was previously a member of the team that founded NSSIF, HMG’s corporate venture arm for National Security, and the CTO for one of the National Security organisations. He has a particular interest in cyber security and the use of data and machine-learning to understand and protect complex systems. Steve is on the advisory board of Exalens and the Royal Holloway School of Business Management and is a Fellow of the IET.
Traditionally ICS were physically segregated from Information Technology (IT) systems. They were two different worlds, rooted in different periods of history. ICS developed as bespoke firmware-based applications evolving to help manage and control mechanical systems used in areas such as manufacturing and petro-chemicals which were rooted in industrial technologies of the late 19th and early 20th centuries. IT systems are by comparison relatively new, developing rapidly from the computer systems that emerged from WW2 and the post-war period.
For larger systems the more common ICS types are SCADA (Supervisory Control and Data Acquisition) which uses networked computers to manage underlying peripheral devices such as PLCs (Programmable Logic Controllers) that are used to monitor and control the electro-mechanical systems, and DCS (Distributed Controls Systems) which are process control systems usually based on proprietary code integrating a network of plant controllers and sensors. These systems emerged in the 1960s and 1970s, at a time when networked and distributed IT computing was only just starting to emerge with ARPANET – the pre-cursor to the Internet – appearing in 1971.
It was only a matter of time before the two distinct worlds would start to merge. People saw opportunities to move data between the two to provide business and operational benefits, and so interchanges became more common but were often ad hoc to meet specific requirements and not considered as part of an architected systems approach. Such “interfaces” often straddled air-gaps using removeable media such as floppy-disks and USB sticks of questionable provenance.
The flip side of this coin is that the divides between the two worlds were not traversed when they should have been, for example importing software and firmware patches to upgrade components within the controls systems, thereby leaving them vulnerable to attacks that could be orchestrated via the unofficial and unmanaged interfaces previously described.
One of the best known examples of this is Stuxnet and its use in a cyber-attack on the Iranian uranium enrichment programme in 2010. Whilst there is still speculation around this incident, the attack vector would have been removeable media to introduce the computer worm across the air gap and into the network of Windows servers that formed part of the control system. This was achieved through companies in the supply chain, implanting the worm in their systems and waiting for it to reach the intended target through normal operations. Once in the target plant it attacked the software that controlled the programmable logic controllers (PLCs) that were the interfaces to the uranium centrifuges. This caused the centrifuges to spin irregularly, thereby causing significant damage. It is estimated that this attack set back the Iranian uranium enrichment programme by two years.
Over time any segregation between the two worlds has eroded as the requirements to flow data across the divide have grown. The requirements to patch components within control systems, the driving and monitoring of enterprise business process that span IT and ICS, the capturing of management information, have all driven the need to integrate the two worlds.
This has increased the likelihood of cyber-attacks on plant and manufacturing systems as the airgap has been digitally permeated thereby creating attack vectors. Furthermore, whilst IT systems typically enjoy effective cyber defences, ICS are not afforded such protection.
In recent times the Covid-19 pandemic and the war in Ukraine have exposed the fragility of global supply chains. Disrupting supply chains upstream of a target organisation is an effective and often easier way to achieve the desired outcome. There are many examples of this that involve either cyber-attacks on IT or ICS, but in each case the impact was at an organisational level and the blast radius extended into the supply chain beyond the target organisation.
- In 2022 a cyber-attack on IT systems at Kojima Industries shut down communication channels crippling crucial production management functions. This in turn caused Toyota to suspend production as Kojima could not supply components to meet Toyota’s just in time manufacturing model.
- A cyber-attack against Renault-Nissan in 2017 involving the WannaCry ransomware halted production at five plants located in England, France, Slovenia, Romania, and India. To prevent the spread of the infection throughout the company’s corporate environment, the infected plants were disconnected from its network.
- In 2017 Mondelez, a multinational food and beverage company, was the victim of an attack leveraging the NotPetya malware. This attack damaged 1,700 servers and 24,000 laptops, which severely impacted production facilities around the globe.
The approach to the management and securing of these systems has largely remained distinct. This is down to the differences, real or perceived, between the two types of system. The system architectures are different in terms of network topologies and segmentation, and functional partitioning. The physical components are very different in in terms of endpoints, and even where they are the same such as Windows servers, in ICS policy dictates that they are hardened to the extreme with proprietary software installed and so bear little resemblance to their IT counterparts. Furthermore, patching regimes are radically different, with components in ICS typically operational beyond vendor end of life dates and so beyond patch availability.
Lastly, and most importantly, the security objectives for the systems are usually different. IT systems are business systems whose primary security objective is to protect the confidentiality of data, whereas for ICS the integrity of production processes and availability of components is paramount. Protection of information is important, but loss of production translates into loss of output and so revenue.
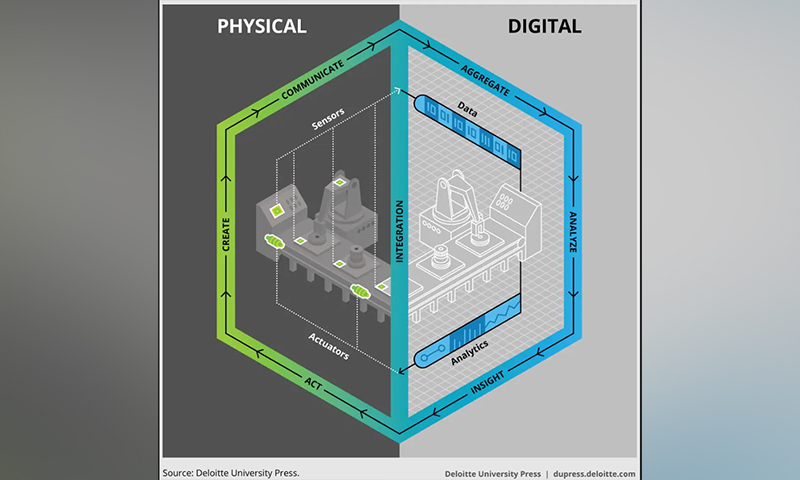
What is needed is systems approach, considering both IT and ICS holistically. Cyber-physical systems (CPS) are the integration of computation, networking, and physical processes of an organisation. Embedded computers and networks monitor and control the physical processes, with feedback loops between these and the business IT systems. The economic and indeed societal potential of these systems is significant; harnessing the power of the data across the system as a whole using AI and ML technology to optimise, automate and protect. The technology builds on embedded systems, integrating the dynamics of the physical processes with those of software and networking, to enable modeling, design, and analysis techniques for the integrated whole.
Cyber-physical systems are complex and dynamic, and it is not just cyber threats that need to be addressed, but also operational resilience. Systems faults and equipment failures, whatever the cause, will result in disruption to operations and therefore impact the business and represent risks to operational availability and therefore business continuity. With IT systems and ICS becoming increasingly integrated, the monitoring and cyber security systems need to span the entire cyber-system to meet the needs of the modern enterprise. Root cause is critical; whilst the impacts can be the same, understanding the root cause will determine how to respond, and this requires monitoring both the cyber and physical aspects of the system. And in order to answer the question of how to respond quickly, the data collected across the system needs to analysed and an answer generated through AI technology. Cyber-physical systems, therefore, need cyber-physical monitoring, and automated detection and response for an holistic operational resilience approach. The corollary of this is that the support teams need to be brought together so that system owners (information and operational) know how to respond and why.
Cyber-physical systems and therefore cyber-physical monitoring are the future. It has been shown that the integration of cyber and physical (IT and ICS) is inevitable. And it is not just manufacturing and industrial. Cyber-physical systems are increasingly prominent in all aspects of our lives, from smart cities and homes to the vehicles we drive and travel on. We can and should no longer make the distinction, and indeed embrace the benefits and advantages that true cyber-physical systems bring. To achieve this we must also recognise that we need the new generation of cyber-physical monitoring tools that exploit AI to make sense of the data and enable timely decision-making when time is of the essence.






